6 Proven Cybersecurity Practices Every Company Should Follow in 2025

Introduction
Cybersecurity Practices 2025 are no longer optional they’re essential for every company aiming to stay safe in today’s digital world. From advanced phishing attacks to ransomware, threats are evolving fast. That’s why businesses must adopt proven security strategies to protect data, customers, and operations. In this guide, we’ll explore 6 proven Cybersecurity Practices 2025 that every company should follow to build resilience against modern cyber risks.
For IT agencies like LogicNosh, protecting client data isn’t just a service—it’s a responsibility. Businesses that fail to prioritize cybersecurity risk financial losses, legal liabilities, and reputational damage that can take years to repair.
To help you stay protected, here are 6 proven cybersecurity practices every company should follow in 2025.
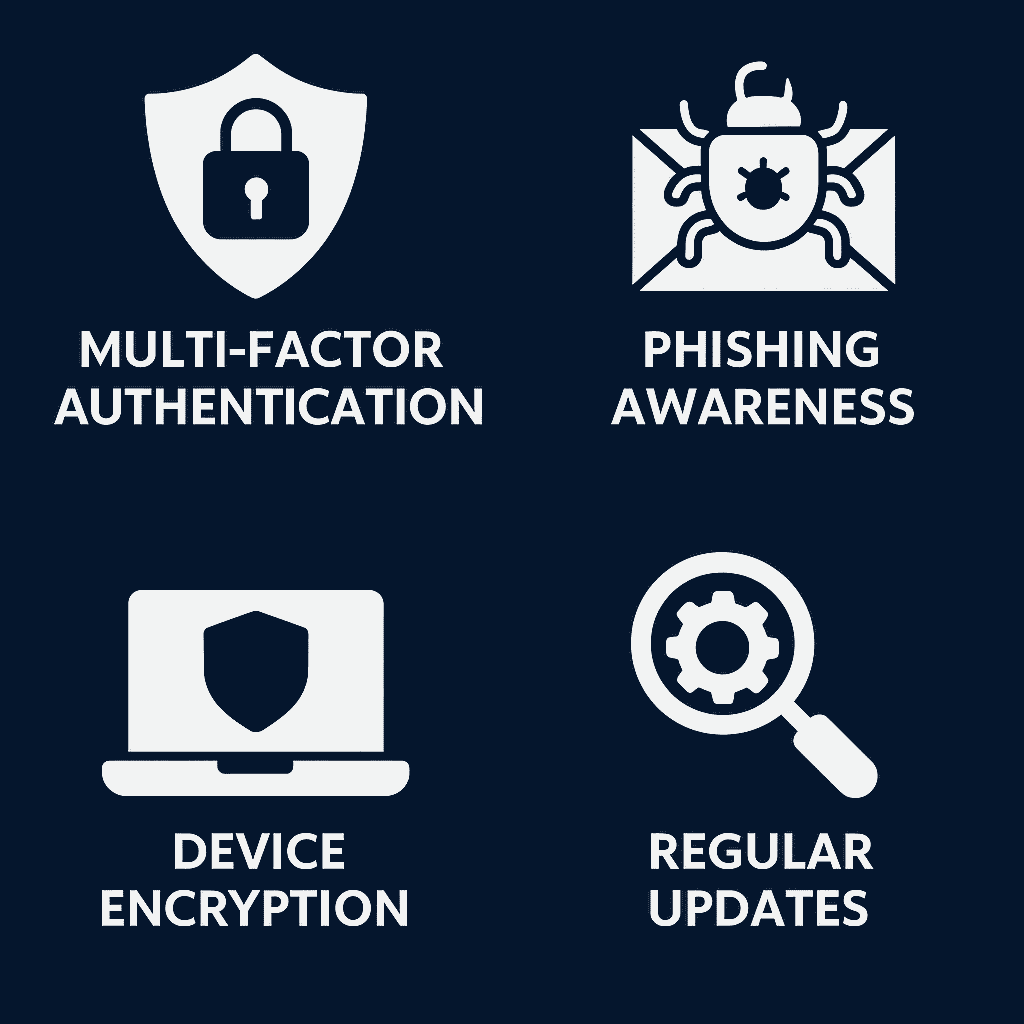
1. Implement Multi-Factor Authentication (MFA) Everywhere
Passwords alone are no longer enough. With phishing attacks becoming more sophisticated, even the strongest passwords can be compromised.
🔑 Why MFA Matters in 2025
- Adds an extra layer of security beyond passwords.
- Prevents unauthorized logins even if credentials are stolen.
- Reduces risk of ransomware and account takeovers.
Best Practices:
- Use MFA on all critical systems (email, CRM, cloud apps, payroll).
- Prefer app-based authenticators (Google Authenticator, Authy) over SMS codes.
- Regularly audit login attempts and enforce MFA compliance.
According to Microsoft, MFA can block over 99% of automated cyberattacks.
2. Adopt a Zero Trust Architecture
The old “trust but verify” approach doesn’t work anymore. In 2025, the motto is “never trust, always verify.”
Zero Trust means every device, user, and connection must be verified continuously—whether inside or outside your network.
Why Zero Trust Is Essential:
- Limits lateral movement in case of a breach.
- Protects against insider threats.
- Ensures compliance with GDPR, HIPAA, and other data protection laws.
Steps to Adopt Zero Trust:
- Segment networks to reduce exposure.
- Enforce least-privilege access (only give employees the access they need).
- Continuously monitor traffic and behaviors with AI-driven tools.
Outbound link: NIST Zero Trust guidelines
3. Use AI-Powered Threat Detection
Cybercriminals are already using AI to launch smarter phishing campaigns and evade traditional security tools. Businesses must fight fire with fire by leveraging AI-powered cybersecurity.
Benefits of AI Security in 2025:
- Detects unusual activity in real-time.
- Predicts potential breaches before they occur.
- Automates responses to common threats, saving IT resources.
Examples of AI-driven tools:
- Darktrace
- CrowdStrike Falcon
- Cisco SecureX
These tools analyze patterns across massive datasets to detect threats that humans might miss.
4. Train Employees Against Social Engineering
Human error remains the #1 cause of data breaches. In 2025, phishing, smishing (SMS phishing), and deepfake scams are more advanced than ever.
Why Employee Training Is Critical:
- 82% of breaches involve a human element (Verizon DBIR).
- Social engineering attacks are getting harder to spot.
- A single careless click can cost millions.
Best Practices for Employee Awareness:
- Run quarterly phishing simulations.
- Provide short, engaging cybersecurity training modules.
- Establish a “report phishing” button in your company email.
Remember: technology can protect systems, but trained employees protect businesses.
5. Regularly Update & Patch Systems
Outdated software is a hacker’s best friend. Unpatched vulnerabilities were behind major cyberattacks like WannaCry, which affected 200,000 computers worldwide.
In 2025, patch management is non-negotiable.
Action Plan:
- Automate patching wherever possible.
- Maintain an updated inventory of all devices and applications.
- Prioritize critical security patches over feature updates.
Pro tip: Use tools like ManageEngine Patch Manager Plus or WSUS to streamline updates.
6. Encrypt Data & Back It Up
Data is the lifeblood of every business. But without encryption and secure backups, it’s a hacker’s playground.
Why Encryption & Backups Matter:
- Protects sensitive data in case of interception.
- Ensures business continuity during ransomware attacks.
- Meets compliance requirements in multiple industries.
Cybersecurity Practices 2025:
- Use end-to-end encryption for customer data.
- Store backups in multiple locations (cloud + offline).
- Regularly test recovery processes.
Outbound link: OWASP Data Security Principles
How to Implement Cybersecurity Practices 2025 Step by Step
- Practical guide: start with audits, then MFA, then employee training, etc.
- Helps readers feel actionable.
The Business Case for Strong Cybersecurity
Cybersecurity isn’t just about defense it’s about competitive advantage. Companies that demonstrate strong security earn more trust from customers, investors, and partners.
For IT agencies like LogicNosh, integrating advanced cybersecurity practices into client solutions isn’t optional it’s the foundation of sustainable growth.
Internal link: See our guide on Custom Web App Development to learn how we build security into every project.
FAQs
Q1: What is the most important Cybersecurity Practices 2025?
👉 Multi-Factor Authentication (MFA) remains the single most effective step for preventing unauthorized access.
Q2: Is Zero Trust only for big companies?
👉 No. Even small businesses benefit from Zero Trust since cybercriminals increasingly target SMBs with weaker defenses.
Q3: How can startups afford advanced cybersecurity tools?
👉 Many providers offer scalable, pay-as-you-go models. Startups can begin with essentials (MFA, patching, employee training) before investing in AI tools.
Q4: How often should companies train employees?
👉 At least quarterly, with micro-trainings for new threats (like AI-generated phishing emails).
Q5: What industries need Cybersecurity Practices 2025?
👉 Every industry is at risk, but healthcare, finance, and e-commerce are the top targets due to sensitive data and high transaction volumes.
Conclusion
Cyber threats in 2025 are faster, smarter, and more damaging. But with 6 proven cybersecurity practices—MFA, Zero Trust, AI-powered defense, employee training, patch management, and data encryption—businesses can significantly reduce their risks.
If you want expert support in securing your digital infrastructure, LogicNosh IT Agency can help. We specialize in building scalable, secure, and future-ready IT solutions that keep your business one step ahead of attackers.